Enigma's Secrets How it Worked and How the Code was Broken By way of introduction, see the Historical Background to Enigma and the Key Players Involved The Working Principle The Enigma machine basically provided a simple substitution of a plaintext symbol with a different ciphertext symbol generated by the machine What made the machine special however was that 23 October 21 Codewords are like crossword puzzles but have no clues!So initially, the total number of inputoutputs for the Enigma Machine (individual monoalphabetic ciphers) was 6 326!
The World According To Benedict Cumberbatch Enigma Chapter 3 The Substitution Cipher
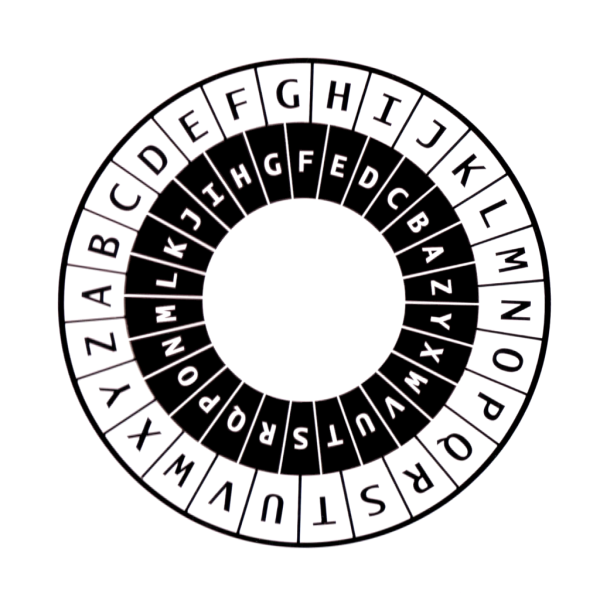
Easy alphabet enigma code
Easy alphabet enigma code-However, this number is only a measureEnigma unbreakable The Poles had broken Enigma as early as 1932, but in 1939, with the prospect of war, the Poles decided to inform the British of their successes Dilly Knox, one of the former British First World War codebreakers, was convinced he could break the system, and set up an Enigma Research Section, comprising



1
10 Codes and Ciphers Commonly Used in History Code language has been used to safeguard and conceal important messages for thousands of years As time progressed, complex codes have been created since simple codes are easily decoded Codes and ciphers are not the same In code, each word in the message is replaced by a code word or symbolCode Breaking and Decoding Tools The following codes and ciphers are detailed below, click to go straight to one or carry on reading Modern Codes, Atbash Cipher, Caesar Shift, Caesar Square, Anagrams, Substitution Ciphers, Other Ciphers Creating and decoding secret messages has played a pivotal role throughout history and in many fictional novels, from the Caesar Cipher byEnigma 00 updates the Enigma algorithm for the twentyfirst century Like the original Enigma, E2K is a polyalphabetic cipher each plaintext letter is mapped to a ciphertext letter by means of a permuted alphabet Unlike the original Enigma, the permuted alphabet at each plaintext position is not determined by a series of rotors
This paper includes a C program that simulates Enigma, and a method to break its code The latter is achieved by a simulation of a simplified Bombe, a mechanical device that was actually used during WWII at Bletcheley Park, a site in England where a major deal of the work on breaking Enigma's code was done The mathematical prowess of the Polish Cypher Bureau had secretly first broken Enigma codes in 1932, with the aid of French intelligence At the eve of the war they handed their work to the Allies The kit—called the Enigma Mark 4—was created by S&T Geotronics as an opensource was soldering the LED lights that form the Enigma machine's alphabet display behind Morse code The
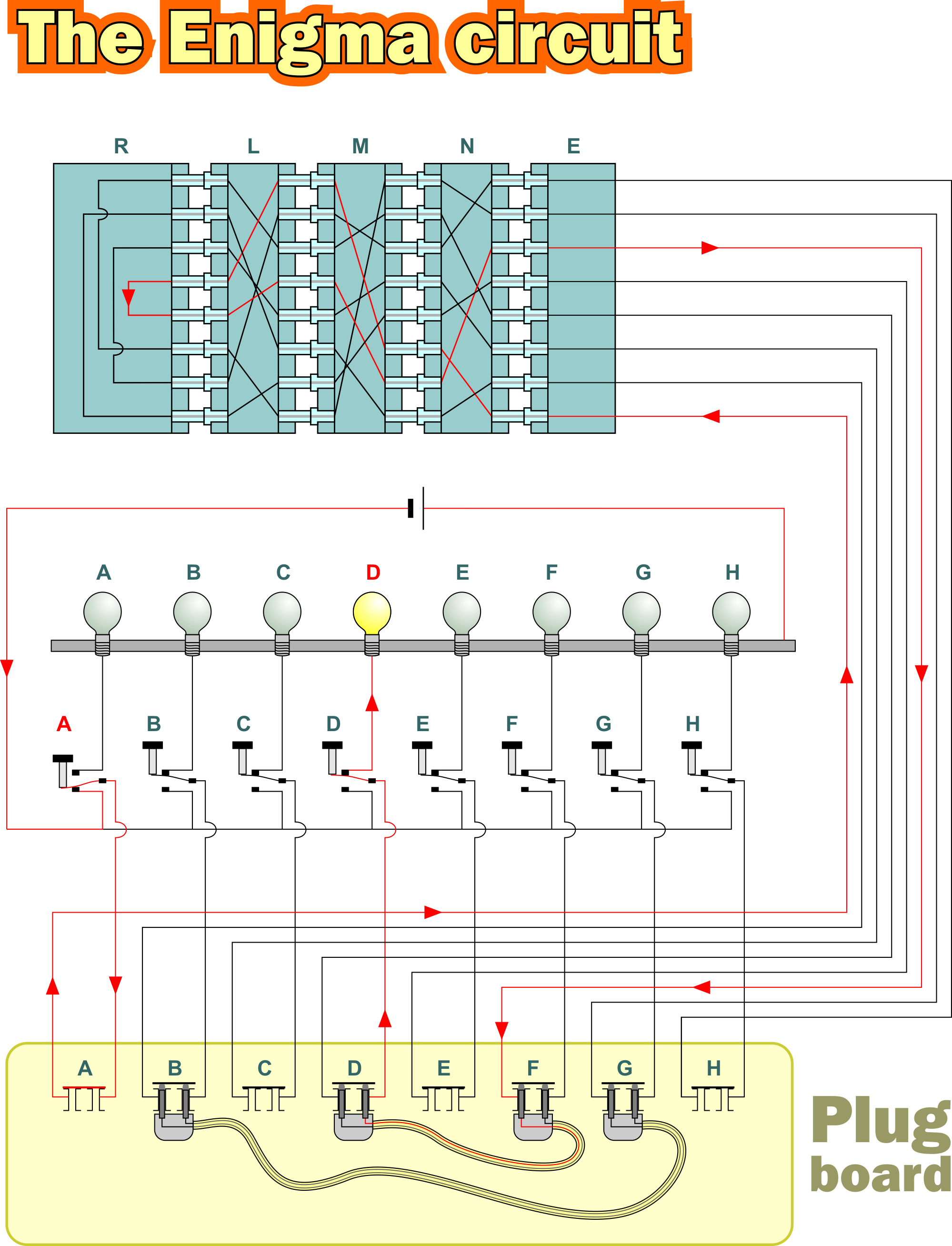
And so on, through the alphabet Now, when you write your message, every time you have the letter A, you replace it with a Z, when you have a letter B, you replace it with a Y But there's some bad news about this code Not only is it easy to encode, it's easy to decode, too! Image Source enigmalouisedadecouk As mentioned earlier, the Enigma Machine is an electromechanical device, which works through mechanical parts as an electric current passes through it The machine consists of four main components keyboard, plugboard, lampboard and rotors When you press a key on the keyboard (L, for example), an electricIt is completely impossible to create an impossible code However most people come up with a very simple code'a' = 'b', 'b' = 'c' and so on The famous enigma code did not do this It came up with an alternative way to substitute letters Here is a simplistic version of it



Enigma The German Cipher Machine




How Did The Enigma Machine Work Computing The Guardian
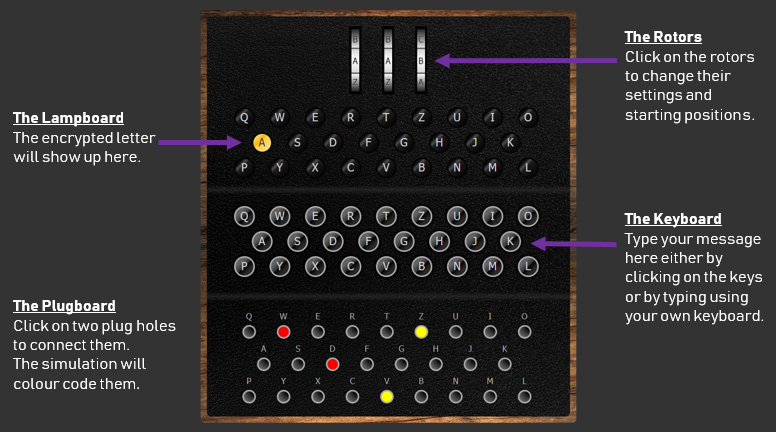
Morse Code Translator is a translator that lets anyone translate text to Morse code and decode Morse code to text easily With the online Morse code translator, anyone can convert any plain text in English or whatever language to Morse code and vice versa The Enigma machine is a complicated apparatus consisting of a keyboard, a set of rotors, an alphabet ring, and plug connections, all configurable by the operator For the message to be both encrypted and decrypted, both operators had to know two sets of codes A daily base code, changed every 24 hours, was published monthly by the Germans The Enigma was constantly updated throughout the war, so the exact types of settings variedHowever, they usually included The rotors The Enigma M1 had three rotors that the operator could choose from from a pool of 5, though this number was later increased to 8 (and a machine with 4 rotor slots was released toward the end of the war) You



1




The Enigma Machine And The Ultra Secret South African Military History Society
This code, while fairly straightforward, is an easy way to begin assigning symbols to your alphabet Write out the alphabet in its standard order After this, go through and number each letter of the alphabet from 1 to 26 so that A=1, B=2, and complete this pattern This code, while fairly simple, is also easy to crackEnigma decoder Decrypt and translate enigma online The Enigma cipher machine is well known for the vital role it played during WWII Alan Turing and his attempts to crack the Enigma machine code changed history Nevertheless, many messages could not be decrypted until today Alphabetical substitution Hex to Base64Tool to decrypt/encrypt with Caesar Caesar cipher (or Caesar code) is a shift cipher, one of the most easy and most famous encryption systems It uses the substitution of a letter by another one further in the alphabet



The World According To Benedict Cumberbatch Enigma Chapter 3 The Substitution Cipher



The Polish Attack On Enimga
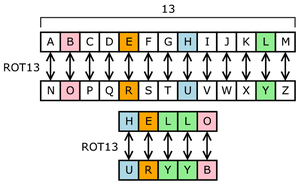
Enigma CS61B fa21 classproject The Enigmas effect a substitution cipher on the letters of a message That is, at any given time, the machine performs a permutation—a onetoone mapping—of the alphabet onto itself The alphabet consists solely of the 26 letters in one case (there were various conventions for spaces and punctuation)The maths comes if you think of the letters as numbers from 0 to 25 with A being 0, B being 1, C being 2 etc Then encoding, shifting the alphabet forward three places, is the same as adding three to your starting numberThe Caesar cipher encrypts by shifting each letter in the plaintext up or down a certain number of places in the alphabet If the message was right shifted by 4, each A would become E, and each S would become W like the Enigma machine but once the code is broken, it's extremely easy to figure out the plaintext The Caesar cipher is



Enigma Procedure



Enigma Cipher
Enigma machines use a form of substitution encryption Substitution encryption is a simple approach to encrypt communications, but it's also pretty easy to crack A Caesar cypher is a simple example of a substitution encryption technique Each letter of the alphabet is shifted to a certain number of places in a Caesar cypherAlphabet The display windows at the top of Figure 1 show the letters JLY The three encoding is reversible also makes life easier for anyone trying to break the Enigma code Breaking the Enigma code which were easy to guess if you knew the weather at the point of transmission This code can be represented using the mapping x → x 2 where x stands for the position of the letter in the alphabet So k, with position number 10, becomes M with position number 12Towards the end of the alphabet, y would go to the letter with position number 24 2 = 26 but 25 is the maximum position number as there are only 26 letters in the alphabet and we



Substitution Cipher Wikipedia



Enigma Machine By 101computing Net
CryptiiEnigma to Text Cryptiiv2 Cryptii Convert, encode, encrypt, decode and decrypt your content online Attention! The encryption code returns an element from the alphabet array The Caesar cipher is probably one of the most basic ciphers, although it was the basis of the Enigma codeUse your understanding of the English language to deduce which letter of the alphabet should be allocated to which number When you have allocated a letter to a number add it into the relevant numbered box in the grid below the Enigma code That letter will automatically appear in all of the corresponding numbers on the main grid




The Enigma Machine And The Ultra Secret South African Military History Society



2
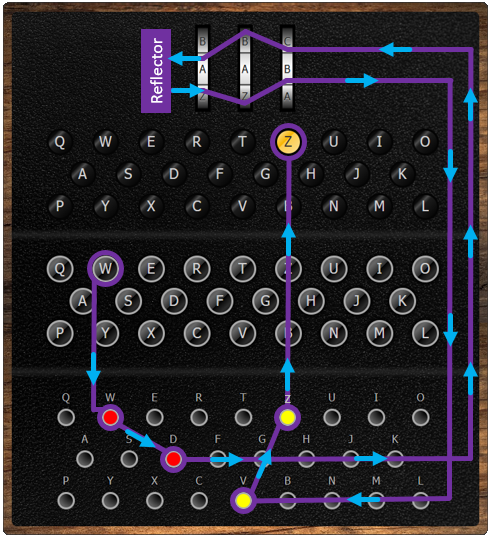
Acknowledgements) Retraced some links— Website history External Video Universal Enigma in action, and a basic tutorial here (courtesy of poughkeepsieblue) — Dec 13The Enigma rotor cipher machine was potentially an excellent system It generated a polyalphabetic substitution cipher, with a period before repetition of the substitution alphabet that was much longer than any message, or set of messages, sent with the same key A major weakness of the system, however, was that no letter could be enciphered to itselfAnswer (1 of 2) Really simple I have written an Enigma routine that easily runs on LuaJIT or Lua and have put that on the internet for usage for everybody It's open source and comes with a packet of additional software, that is fun and useful code > echo der angriff ist im morgengrauen /




How To Build An Enigma Machine Virtualisation In Python By Vasile Păpăluță Analytics Vidhya Medium




The Enigma Enigma How The Enigma Machine Worked Laptrinhx
This version of cryptii is no longer under active development Find the latest version on cryptiicom Cryptii is an OpenSource web application under the MIT license where you can encode and decode between different formatTo start you off, we reveal the codes for two or three lettersEnigmas Of The English Alphabet is very strongly recommended, especially to readers new to the English language, as well as those who are searching for a "userfriendly" and easytofollow guide to the many diversities and specifics of a language that even nativeborn speakers can have difficulties with Read more



Enigma Encoder 101 Computing



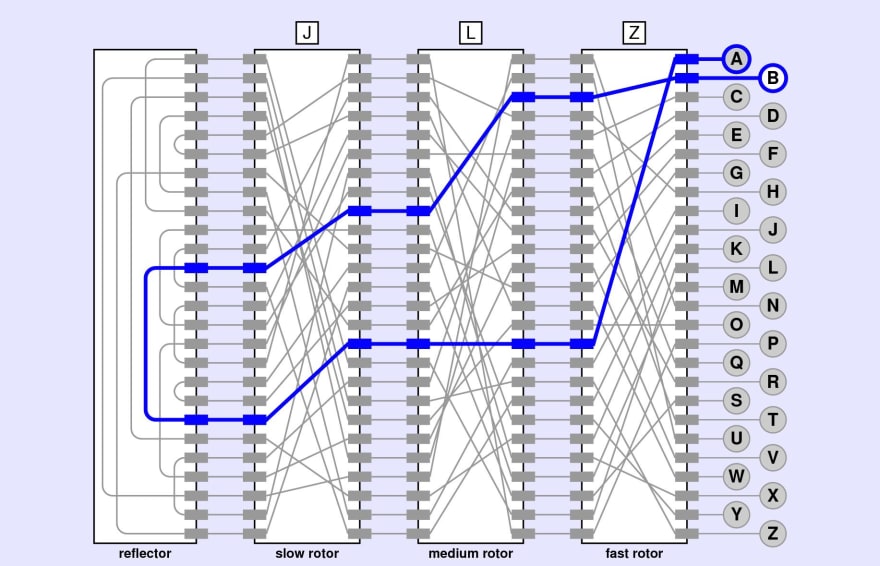
5 0 The Mechanization Of Ciphers
Simplified Enigma machine that is limited to a six letter alphabet Figure 4 Simplified version of a Enigma machine with one rotor The disk on the left is the keyboard, the middle ring is the rotor, and the disk on the right is the lampboard The wiring of the rotor determines how the plaintext letters will be encrypted The three rotors in the Enigma machineSourceWikipedia The military Enigma Machine had another set of encryption layers by using switchboards where each alphabet got mapped to another alphabet The enigma keyboard The user interface is very simple — it is represented by a keyboard of 26 letters It is used to insert the input in the machine



The World According To Benedict Cumberbatch Enigma Chapter 3 The Substitution Cipher




The Enigma Cipher Machine And Breaking The Enigma Code
3 ENIGMA CODE is a sophisticated cipher used by Germans during World War II It involved the use of an Enigma machine (which is very similar to a type writer), and all Germans had the same type of machine and the initial wheel configuration in the machine which was used to communicate with all the teams Apply your code book to messages Use the code words in your code book to encode messages You may find that you can save yourself time by leaving nouns (like names and pronouns like I, me, she) as plain text However, this decision depends purely on your situation Twopart codes apply two different code books to encode or decode a message The key to a successful simulation of the ENIGMA machine is to know the internal wirings of the rotors (or "wheels"), shown below The rotors are labeled I through VIII, b, and g The letters of the alphabet in order represent the input, and the wiring for each rotor indicates the transformation for each letter




Charlesreid1




The Enigma Cipher Machine And Breaking The Enigma Code
An Enigma machine is a famous encryption machine used by the Germans during WWII to transmit coded messages An Enigma machine allows for billions and billions of ways to encode a message, making it incredibly difficult for other nations to crack German codes during the war — for a time the code seemed unbreakable Alan Turing and other researchers exploited aA code is a system of symbols, letters, words, or signals that are used instead of ordinary words and numbers to send messages or store information o Learn more about the code machine, ENIGMA, Write one letter of the alphabet in each division on each wheel Then attach the two wheels together using a split pin so that you can rotateAnswer (1 of 5) Enigma was particularly difficult to break because it combined two different types of encryption, each of which had different vulnerabilities The rotors take in a letter and output a different letter, then rotate so that the encryption pattern is different for each time a lette



The World According To Benedict Cumberbatch Enigma Chapter 3 The Substitution Cipher




Digitalocean Blog
The Enigma Steckerbrett (plug board) contains 26 sockets, one for each letter of the alphabet In theory, any number of patch cables could be used on the Steckerbrett, between none and 13 with the mathematical optimum at 11 cables In practice however, most of the German procedures dictated the use of 10 patch cables at all times This meant that exactly 10 pairs of letters wereEasy as 1, 2, 3 This all seems very clever, but so far it's all been letters and no numbers So where's the maths?Because all you have to do to decode it is do the process all over




Enigma Encoder 101 Computing



Why Did The German Nazis Decide To Design Enigma So That It Wasn T Possible To Map A Plain Text Character To The Same Character In The Cipher Text Quora
This is somewhat simpler than the real Enigma machines that used three or four rotors which could be rearranged and selected from a selection, and generally featured a plugboard as well However, we do use an alphabet with n=72 instead of n=26, so The need to conceal the meaning of important messages has existed for thousands of years Over time, people have found increasingly complex ways of encoding their messages as the simpler ways are decoded with greater ease Contrary to laymanspeak, codes and ciphers are not synonymous A code is where each word in a message is replaced with a code word orBuild your own Enigma These pages are about an electronic replica of the famous Enigma cipher machine, that you can build yourselfIt is known as the EnigmaEIf you already own an EnigmaE but haven't yet registered it, now may be the time to do soIf you have any questions whilst building the kit, you might want to check the FAQ or visit the special support page



Enigma Machine Kata




Enigma Code Breaking Replicating A 1930s Polish Cyclometer Hackster Io
28position wheels, Swedish alphabet, trivial ringsetting Changelog Website Minor text updates regarding UE v26 (Features;ˇ106 1016 By 1939, increases in the number of rotors and plugboard pairs had increased this gure 159 10 As you can imagine, breaking the enigma code was quite a task! The enigma machine was used in World War II to encrypt secret messages The Enigma machines are a series of electromechanical rotor cipher machines The first machines were invented at the end of World War I by German engineer Arthur Scherbius and were mainly used to protect commercial, diplomatic and military communication Enigma machines became




Top 10 Codes And Ciphers Listverse



Enigma Machine How Does The Famous Encryption Device Work Dev Community
Since there are 26 letters in the alphabet, there are only 25 other options A Caesar cipher is one simple type of monoalphabetic cipher a class of ciphers where the whole code is based on one letter of the alphabet standing in for another letter consistently throughout the whole message Basically you just scramble the alphabetInstead, every letter of the alphabet has been replaced by a number, the same number representing the same letter throughout the puzzle All you have to do is decide which letter is represented by which number!




The Imitation Game How Did The Enigma Machine Work Science Abc




How To Decipher A Secret Code 13 Steps With Pictures Wikihow




Kid S Game To Arduino Enigma Machine 10 Steps With Pictures Instructables




Enigma Machine How Does The Famous Encryption Device Work Dev Community




Caesar Ciphers



2



1



2
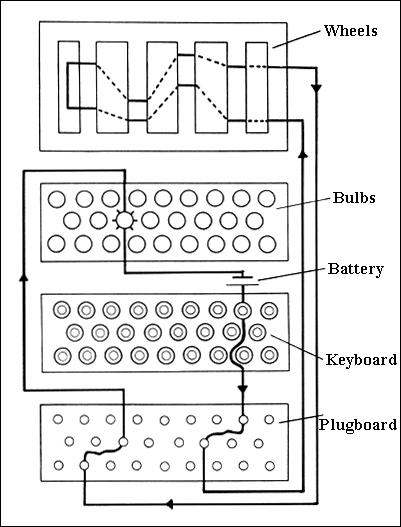



Enigma Machine




Top 10 Codes And Ciphers Listverse



2




Building The Enigma Machine In Swift Agostini Tech




Pin On Cryptography
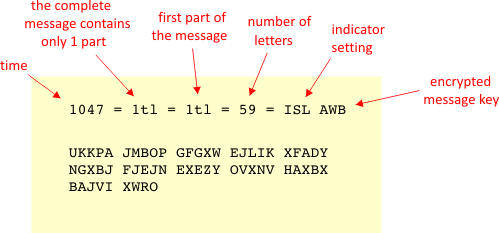



Enigma The German Cipher Machine
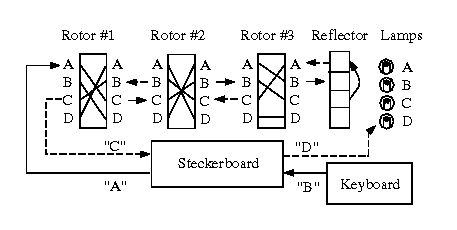



Cryptology I Vigenere Based Systems




Enigma Machine Brilliant Math Science Wiki




The Human Errors That Defeated Enigma Openmind



2




Enigma Machine Simple English Wikipedia The Free Encyclopedia
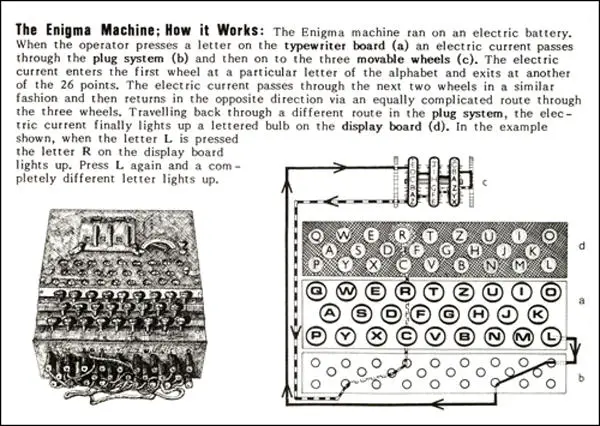



Enigma Machine




Building The Enigma Machine In Swift Agostini Tech




Pigpen Ciphers And Codes Alphabet Code Coding
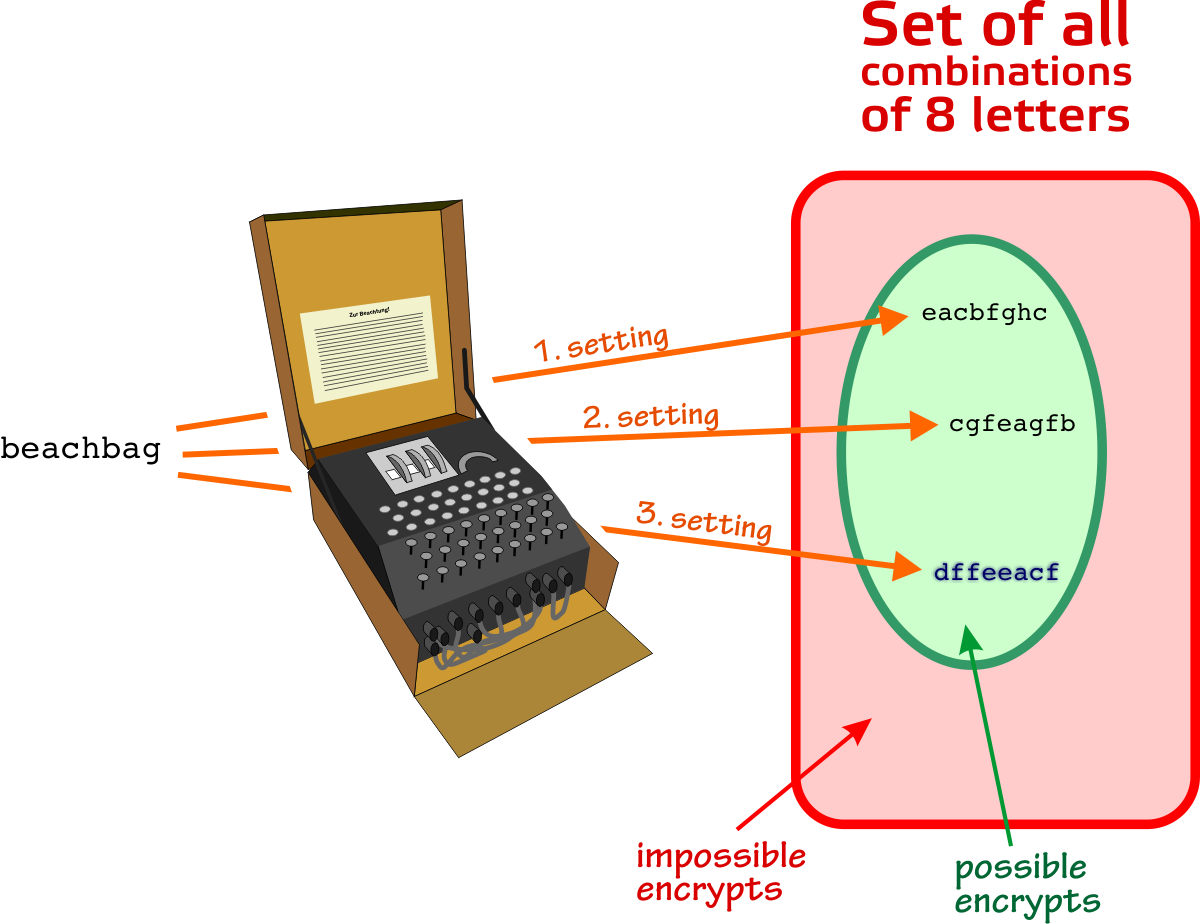



Enigma The German Cipher Machine




Digitalocean Blog



2
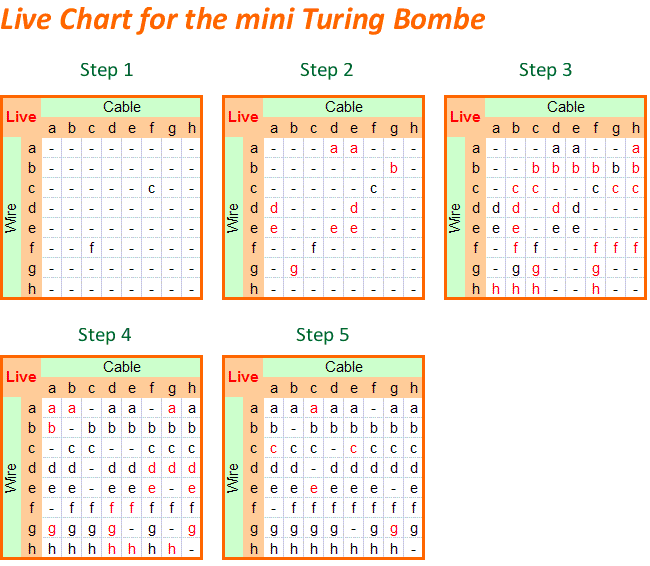



Enigma The German Cipher Machine




Cryptanalysis Of The Enigma Wikipedia




The Enigma 1




Cipher Machines Columbus State University




Pin On Enigma




The Enigma Cipher Machine And Breaking The Enigma Code



2




Vegetarian Pig Lover A History Of Codes And Ciphers In Code And Cipher




How The Allies Cracked The Enigma Code By Karthick Nambi Lessons From History Medium
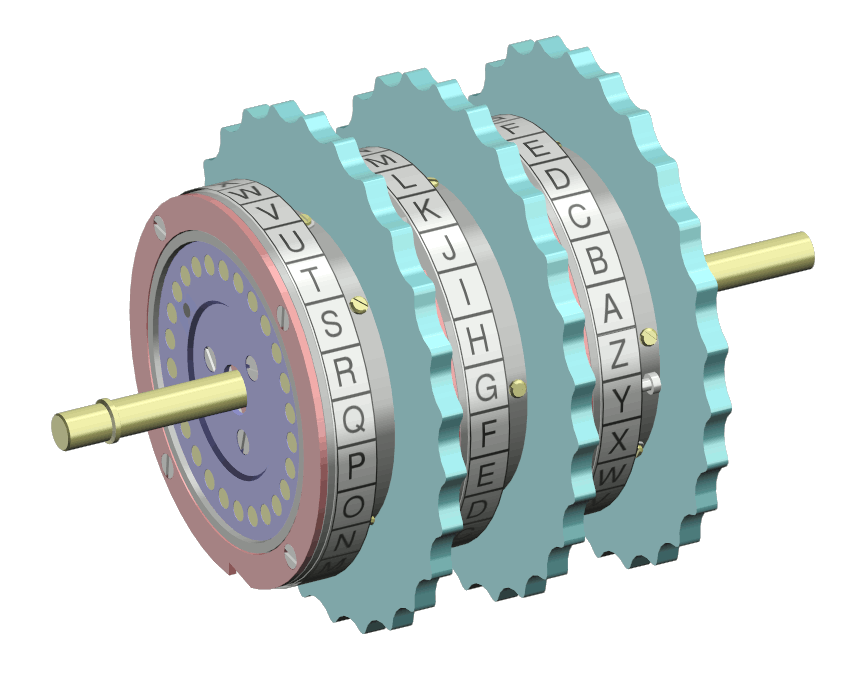



Rotor Machine Wikipedia



Why Cant A Letter Ever Map To Itself In An Enigma Machine Quora



1



Understanding The Enigma Swimming The Styx




The Human Errors That Defeated Enigma Openmind




Rotor Machine Wikiwand



Enigma Paper Enigma Franklin Heath Ltd Wiki




Decoding The Project Languages Code And Ciphers Richard Gallon We Are Here




Project 1 Enigma




A1 Enigma
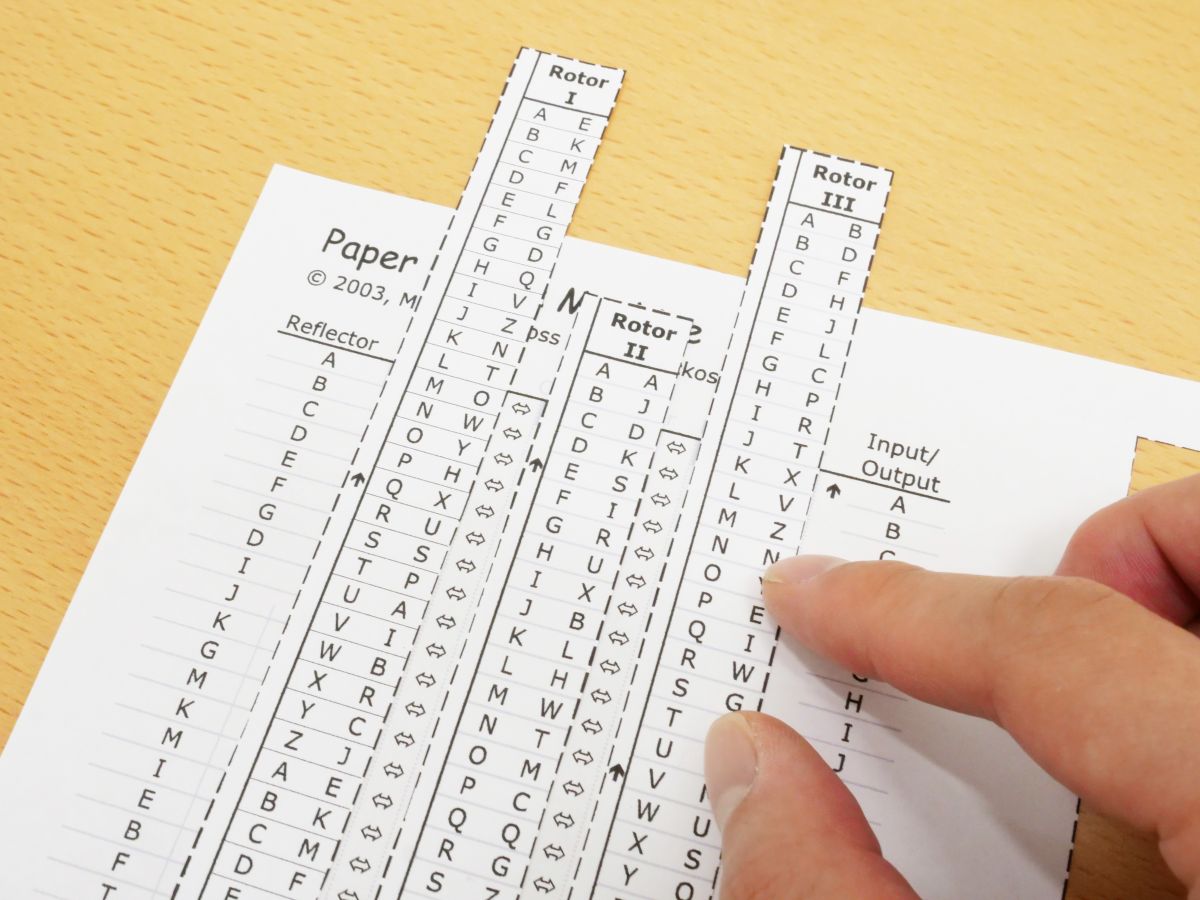



I Tried Using Paper Enigma Machine Which Can Reproduce Nazi Germany S Masterpiece Encryption Machine Enigma With Only One Sheet Of Paper Gigazine




11 Cryptographic Methods That Marked History From The Caesar Cipher To Enigma Code And Beyond



Enigma Paper Enigma Franklin Heath Ltd Wiki




Enigma Codeproject



Code Making And Breaking Activities In Scratch Part 1 Blog My Wiki




Exploring The Enigma Plus Maths Org
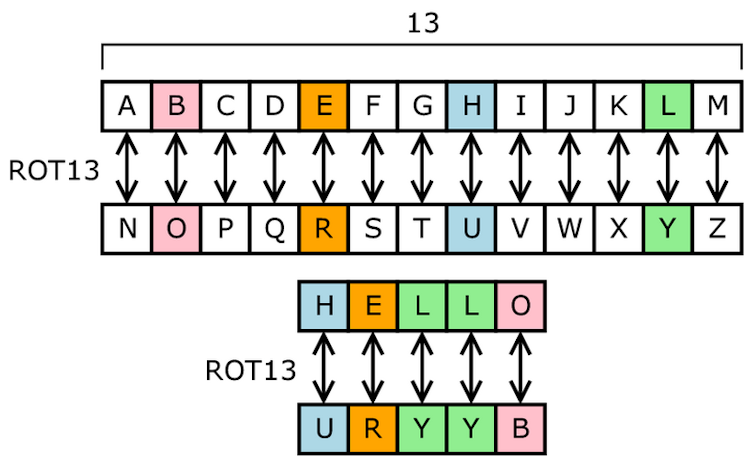



Codebreaking Has Moved On Since Turing S Day With Dangerous Implications
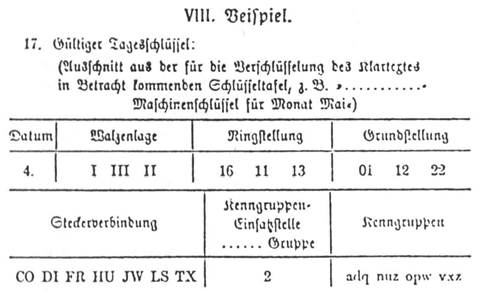



Enigma Codeproject



Alan Turing




The Imitation Game How Did The Enigma Machine Work Science Abc
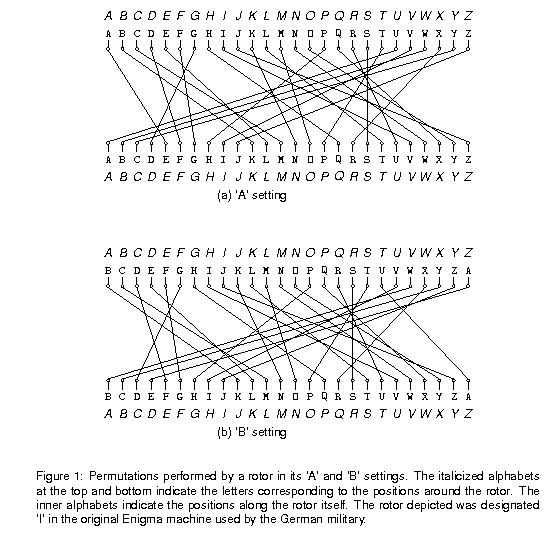



Project 1 Cs 61b Fall 16




Kid S Game To Arduino Enigma Machine 10 Steps With Pictures Instructables
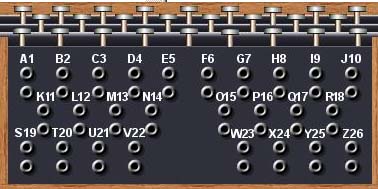



Exploring The Enigma Plus Maths Org
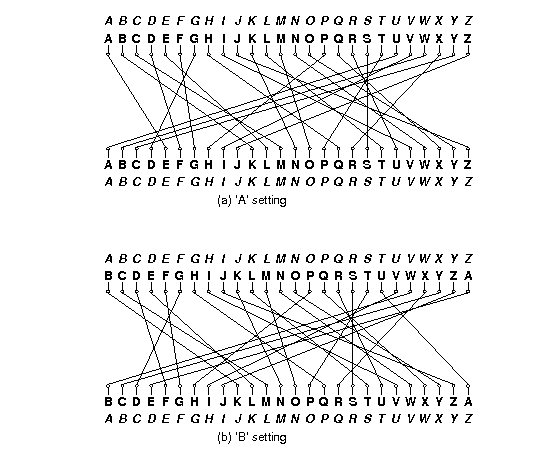



Project 1 Cs 61b Fall 19
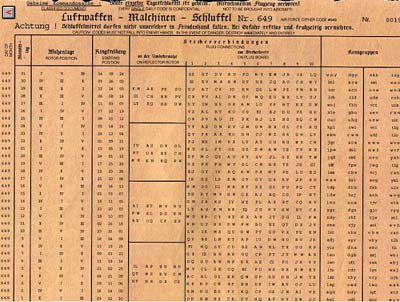



Exploring The Enigma Plus Maths Org
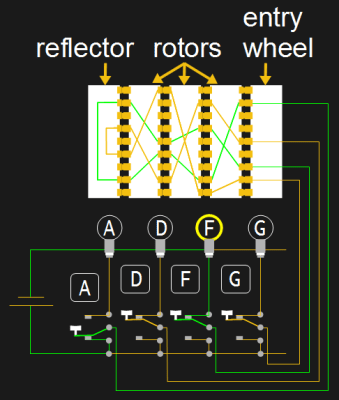



The Enigma Enigma How The Enigma Machine Worked Hackaday




Four Integrated Enigma Theme Ciphers Elgar S Enigmas Exposed
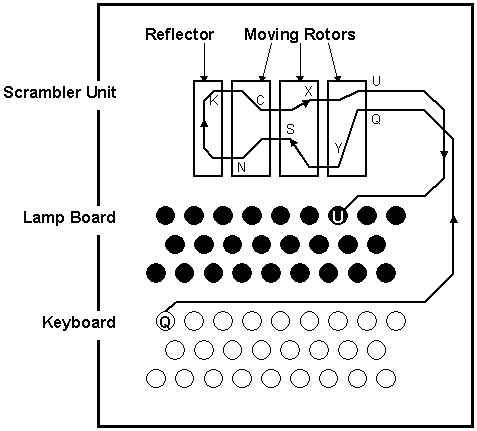



Enigma And A Way To Its Decryption




Code And Ciphers Julius Caesar The Enigma And The Internet




Polyalphabetic Cipher Wikipedia




Ic211 Oop And Enigma
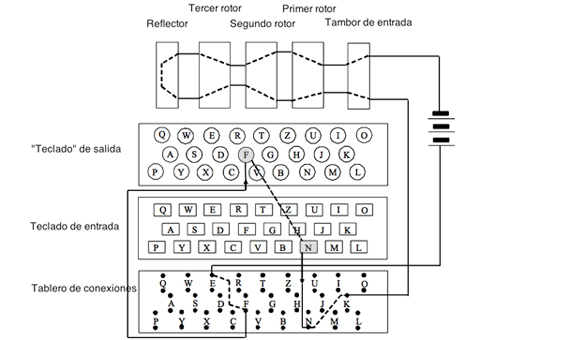



The Human Errors That Defeated Enigma Openmind




How The Allies Cracked The Enigma Code By Karthick Nambi Lessons From History Medium




11 Cryptographic Methods That Marked History From The Caesar Cipher To Enigma Code And Beyond
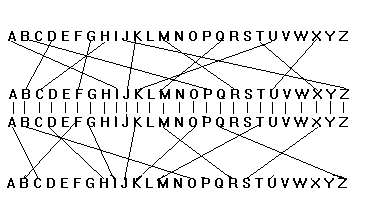



The Enigma 1



Enigma Details




The Enigma Cipher Machine And Breaking The Enigma Code
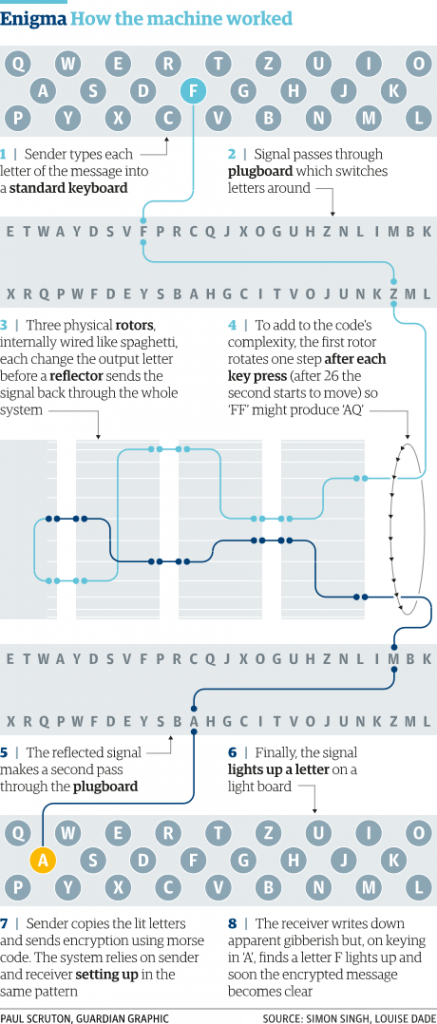



The Imitation Game How Did The Enigma Machine Work Science Abc




How To Crack The Enigma Code Calculate
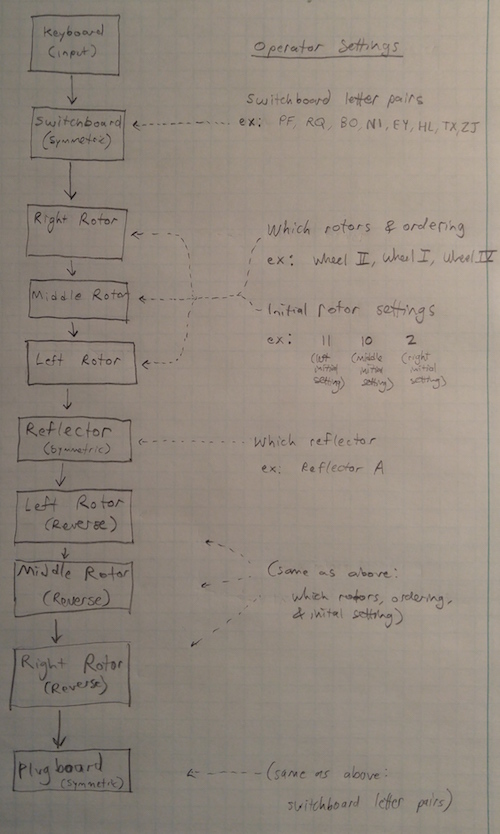



Charlesreid1
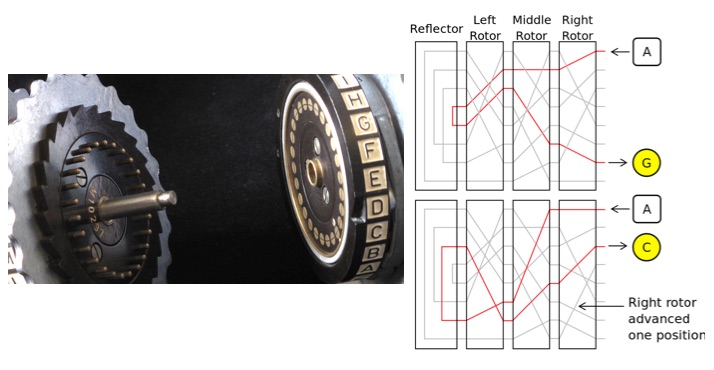



Q How Good Is The Enigma Code System Compared To Today S Publicly Available Cryptography Systems Ask A Mathematician Ask A Physicist



Why Cant A Letter Ever Map To Itself In An Enigma Machine Quora



0 件のコメント:
コメントを投稿